16. Backup and Recovery
Backup and Restore functions of windows server backup
Windows provides Backup and Restore services which are immensely useful when it comes to data lost, or need of formatting the system, or stolen devices etc.
There are four type of backups you can create in windows 1) Incremental Backup 2) Full Backup 3)Differential Backup 4)Mirror Backup.
In this lab, we created one dynamically expanding virtual hard disk to create a backup so that it will use the available space automatically when there is a need to expand that data partition and then created secondary disk for storage purpose and then performed a scheduled backup and single backup.
After performing the backup, windows server can now perform the recovery/restore.
The protection windows server backup provides.
Performed Backup generally be stored as a backup disk image or a file. To protect that file or disk image from third party users, you can use encryption method on the backup file.
The backups can also be protected by password(it is not built in though the user can implement password protected backup in windows).
15. Data Encryption
The functions of bit locker used in lab
It is a storage encryption method that provides the protection to the hard drive(kind of an offline attack). It gives the feature like disk encryption for the hard disk data security. Based on the lab, it is a group policy object to prevent the hard disk data loss for the authenticated users in the network.
Once, the bitlocker gpo is created, when a user will try to access the partition on which it is applied, it will ask for a password and then it will create a recovery key which must be stored safely.
The protection bit-locker provides the user
As discussed in the above answer, it provides the security to a disk partition by applying an encryption method on that selected partition in order to protect a data from third party unauthorized users.
How the recovery key should be stored securely
Managing your BitLocker recovery key is the most important part of the encryption process. The recovery key is needed to gain access to the computer when the user forget PIN or have certain hardware problems such as a motherboard replacement or hard drive crash, or even after performing a BIOS update. Without it there is no way to access the data.
In this lab, we created a separate partition to store the recovery key in order to save it safely and bitlocker does not allow to save it to the encrypted drive. So the recovery key must be stored in the different partition with the appropriate safety where it can not be found by unauthorized entities.
14. Implementing DNSSEC
DNS-SEC
DNS is used to convert the human language(Text) into machine language(IP address) but has no authentication process in between so the concept of DNSSEC(Domain Name System Security Extension) rises. It adds a layer of trust on top of DNS hierarchy by providing authentication.
There are two DNS zones: Forward Lookup zone and Reverse Lookup Zone. Forward Lookup Zone is used to covert the Text into IP address and Reverse Lookup zone is used to convert the IP address into text.
In this lab, we created only forward lookup zone and stored it in active directory and added a host into this zone and then we created unauthoritative DNS for hosting the created zone by using powershell and then tried to resolve the server name with IP address and IP address with server name. then we Installed ADDS to store the centralized data in it. and then assigned the signing zone using DNSSEC to give the shared key to authenticated users.
After these completing these tasks, It was the verification of DNS KEY TA by using powershell and then distribute TAs to a secondary domain controller and then check the DNSSEC validation with and without assigning group policies to query a signed zone. Then unsign and re-sign dnssec on the secure zone just to check the functionalities, also checked the unsecured validation on dnssec. To summarize, we used a DNS zone with DNSSEC in the main server. DNS works on hierarchy and uses DNS zoning method to create a secure environment.
13. Implementing a Network Policy Server
Network Policy Server
Network Policy Server (NPS) allows you to create and enforce organization-wide network access policies for connection request authentication and authorization.
You can also configure NPS as a Remote Authentication Dial-In User Service (RADIUS) proxy to forward connection requests to a remote NPS or other RADIUS server so that you can load balance connection requests and forward them to the correct domain for authentication and authorization. NPS allows you to centrally configure and manage network access authentication, authorization, and accounting with the following features : 1) RADIUS Server 2) RADIUS Proxy 3) RADIUS Accounting
The Authentication Method used
NPS is the Microsoft implementation of the RADIUS standard specified by the Internet Engineering Task Force (IETF) in RFCs 2865 and 2866. As a RADIUS server, NPS performs centralized connection authentication, authorization, and accounting for many types of network access, including wireless, authenticating switch, dial-up and virtual private network (VPN) remote access, and router-to-router connections.
Internet service providers (ISPs) and organizations that maintain network access have the increased challenge of managing all types of network access from a single point of administration, regardless of the type of network access equipment used. The RADIUS standard supports this functionality in both homogeneous and heterogeneous environments. RADIUS is a client-server protocol that enables network access equipment (used as RADIUS clients) to submit authentication and accounting requests to a RADIUS server.
A RADIUS server has access to user account information and can check network access authentication credentials. If user credentials are authenticated and the connection attempt is authorized, the RADIUS server authorizes user access on the basis of specified conditions, and then logs the network access connection in an accounting log. The use of RADIUS allows the network access user authentication, authorization, and accounting data to be collected and maintained in a central location, rather than on each access server.
The security policy created
RADIUS proxy, NPS forwards authentication and accounting messages to NPS and other RADIUS servers. You can use NPS as a RADIUS proxy to provide the routing of RADIUS messages between RADIUS clients (also called network access servers) and RADIUS servers that perform user authentication, authorization, and accounting for the connection attempt.
When used as a RADIUS proxy, NPS is a central switching or routing point through which RADIUS access and accounting messages flow. NPS records information in an accounting log about the messages that are forwarded.
The accounting method used
NPS logging is also called RADIUS accounting. Configure NPS logging to your requirements whether NPS is used as a RADIUS server, proxy, or any combination of these configurations.
To configure NPS logging, you must configure which events you want logged and viewed with Event Viewer, and then determine which other information you want to log. In addition, you must decide whether you want to log user authentication and accounting information to text log files stored on the local computer or to a SQL Server database on either the local computer or a remote computer.
12. Wi-Fi Access Point Security
Security Access Management
When you think of an institute like school, Security access management is the key aspect to consider of.
Unauthorized access can be prevented by using different policies like using the IP Filtering, MAC Address Filtering, per user unique pre-shared key, device authentication, user authentication etc.
When a user tries to access the functionality of the institutional network, if the network administrator has gave one of the security policies which is not that easy to breach, the unauthorized user would not be able to log in to access the functionality.
Common Security issues and management
When it comes to a school, the most common security issue would be the wireless network usage by the students in inappropriate manner or breaking the cyber rules etc.
To solve this perticular issue, the one can use wi-fi security policies which is the best way to prevent this kind of network usage. There are plenty of wi-fi security policies available like WPA, WPA2, PEAP, EAP, MS-CHAP etc. The most common used wi-fi security policy is WPA and WPA2 as it gives two types of security, one is personal and the another one is enterprise. WPA2 Enterprise security is used for medium & large institutes while WPA2 Personal security is used for home or small school networks though it is difficult to manage when there are a lot of users in the network. Personal security uses PSK to provide authorization and authentication while enterprise security uses mutual user authentication via Extensible Authentication Protocol.
The another solution for the same issue is IP address and MAC address filtering. MAC address is basically a physical machine name which ca be changed or spoofed easily so it would be better if the institution is using IP and MAC bonding together. So that even if the MAC address has been changed the user will not be accessible for unauthorized functionality. Group policy management can also be used to prevent the students usin malisious websites or content which is actually harmful for them. An institute can provide different class IP address to the students than teachers with the permissions to some extent. This was the actual case in my past institute where I was studying my bachelor degrees. Teachers and Students had the different classes of assigned IP address so that we were not able to search or access some content. Sometimes it is not the proper solution as it blocks some useful websites for study as well.
11. Firewall rules based management
Firewall
Firewall is a software program that examines the incoming and outgoing network traffic and prevents unauthorized access to private network.
Que-1 Discuss the configuration required on a firewall for a web server providing
1. HTTP and HTTPs
HTTP communicates on port 80 and HTTPs communicates on port 443.
2. FTP over TLS/SSL
This protocol works on port 990 for imlicit SSL and port 21 for explicit SSL for the connection used to establish the communication between server and client.
3. SMTP for sending emails from the websites
It uses port 587 as it uses TLS encryption for secure communication. SMTP service for web server is only intended to send emails.
4. Remote Administration.
IIS service is mandatory for remote administration. port 8172 is used for this service in firewall.
Que-2 Discuss the configuration required on a firewall for a database server providing
1. MariaDB
It is a high performance solution created for all-round protection of production and non-production databases from outside and inside threats. It continuously analyzes and filters database traffic and blocks requests that meet forbidden security rules. Deployed in a proxy mode the firewall resides between database and clients and provides real time tracking of user activity and changes made to database tables.
2. MSSQL
It uses the port no. 1433 by default.
3. Remote Administration
Firewall has a remote administrator setting you can enable to allow WMI traffic.
10. Implementing NAT and Open SSH
NAT
Network Address Translation (NAT) is designed for IP address conservation. It enables private IP networks that use unregistered IP addresses to connect to the Internet. NAT operates on a router, usually connecting two networks together, and translates the private (not globally unique) addresses in the internal network into legal addresses, before packets are forwarded to another network.
As part of this capability, NAT can be configured to advertise only one address for the entire network to the outside world. This provides additional security by effectively hiding the entire internal network behind that address. NAT offers the dual functions of security and address conservation and is typically implemented in remote-access environments.
Basically, NAT allows a single device, such as a router, to act as an agent between the Internet (or public network) and a local network (or private network), which means that only a single unique IP address is required to represent an entire group of computers to anything outside their network.
Open SSH
Open Secure Shell (OpenSSH) is a set of computer programs that facilitate encryption for network sessions using a protocol called Secure Shell (SSH). Secure Shell originated as a network protocol for UNIX-based systems, but can also be used in other various ways, including in Microsoft Windows infrastructure.
The Secure Shell protocol is built on earlier designs for covering communications, command line login functions, and other activities on a network. Like other types of modern security, Secure Shell uses public-key encryption methods to authenticate network traffic. Some of the specific features of Secure Shell have to do with how public keys are stored.
OpenSSH is an open-source software that was developed by a volunteer network. It competes with original proprietary software for Secure Shell, and developers argue about the relative security of each type of software.
Que-1 Discuss the use and function of NAT firewall
First of all, a firewall stands like a barrier between a secure and trusted internal network and an “outside” insecure network, such as the Internet. A firewall is either a software appliance or a hardware-based firewall.
The Network Address Translation is a technology used for remapping an IP address space into another one. To make this thing possible, NAT modifies packets’ IP address while they transit across a traffic routing device.
In simple words, every information that transits the internet is actually a packet of data. There are numerous data packets sent back and forth for every request you make. The data packet you send needs to reach an exact address which has an IP address. So, just as you have your own and unique IP address, the destination on the web has a unique IP address as well.
It was specially developed to improve users online security by helping them filter all the incoming traffic. NAT firewall will detect any threat or malicious attempt and it will automatically block it.
Que-2 Discuss two uses of open ssh either on windows or linux.
You can use windows open ssh instead of using putty to connect to the different system remotely.
9. Managing Certificates
Que-1 The role or function of AD certificate Services and CA Web Enrollment
Que-2 Role or function of Key Archival and Key Recovery Agent
Key archiving allows for the recovery of a private key if a users private key becomes corrupted or is lost. Key recovery is often neccessary if a user profile is accidently deleted, a hard disk fails or becomes corrupted, a smart card fails, or a computer is stolen or lost. You can avoid some os these situations if you enable credential roaming. After enabling credential roaming through the certificate services client policy, private keys are stored within ADDS.
Que-3 Explain at least two uses of the user certificate.
A digital certificate(user certificate) is a part of a public key infrastructure, which is a system of digital certificates, certificate authorities and other registration authorities that verify and authenticate the validity of each party involved in an electronic transaction through the use of public key cryptography.
It is used to secure the communications, such as SSL and other secure functions.
User certificates authenticates the user to the server.
8. Understanding PKI Concepts
Objective: Install and configure Active Directory Certificate Services, CRLs.
Active Directory Certificate Services
According to microsoft, AD CS is the “Server role that allows you to build a public key infrastructure (PKI) and provide public key cryptography, digital certificates and digital signature capabilities for your organization.
Que-1 Role of the root CA and Subordinate CA in PKI
You can limit who has certificates that grant access to a system by having an subordinate ca. These subordinate CAs can be private or publicly trusted, depending on the organizations needs. It is an intermediate CA certificate which subordinate certificate issued by the trusted root specifically to issue end-entity server certificates. Since, the primary root CA is not in the browser, the intermediate ca must be installed on the server acting as a chain link between the browser root and the server certificate.
Que-2 Steps to create the subordinate CA private Key and Certificate
When the server is installing the certificate services must be root CA and it will have their own private key. Once the root CA establishes the private key and certificate services, other computers within domain that establishes another certificate and will be joining a root CA certificate.
Que-3 Can the certificate be used on public website? Justify.
As per the lab established in a windows server environment, the certificate is considered a private certificate which are issued by private CAs of a local network.
Que-4 The use of certificate revocation Lists
A certificate revocation list is a list of digital certificates that have been revoked by the issuing certificate authority before their scheduled expiration date and should no longer be trusted.
When web browser makes a connection to a site using TLS, the web server’s digital certificate is checked for anomalies or problems, part of this process involves checking that the certificate is not listed in a certificate revocation list. These checks are cruicial steps in any certificate based transaction because they allow a user to verify the identity of the owner of the site and discover whether the certificate authority still considers the digital certificate trustworthy.
Que-5 Why an organization would use active directory certificate services?
Most every application we run in our datacenters today provides some sort of web-based interface. The problem being we are also seeing a push for security, more specifically ensuring that all our web accessible interfaces are running through SSL and only accessed through https.
Microsoft Certificate server is just a role that we add to a server within our Active Directory environment. What is does is allows us to essentially turn that server into a trusted authority for our domain-meaning we can request and issue certificates from it, install them on our member servers, and we will no longer be nagged by warnings and messages.
7. Password Cracking Tools
Objective use appropriate s/w tools to access the security posture of an organization, deploy mobile devices securely, implement secure systems design
Cain & Abel
Cain and Abel is a password recovery tool for Microsoft OS. It allows easy recovery of various kind of passwords by sniffing the network. The features of Cain & Abel are protected storage, password manager, LSA secrets dumper, Service Manager, Route table Management, SID scanner, Sniffer, Full RDP sessions sniffer for APR, full HTTPs sessions sniffer for APR, full POP3S sessions sniffer for APR, full LDAPS sessions sniffer for APR, MAC Address Scanner with OUI fingerprint, wireless scanner, 802.11 capture files decoder, and many more
PWDump
PWDump is a hack tool that is used to grab windows password hashes from a remote windows computer.
In technical terms, when the program executes, it connects to a remote computer and downloads the following file: pwdservice.exe . next, the program registers the downloaded file as a remote service and the program creates the HKEY registry entry. the program then sends extracted password hashes to a remote computer.
Que-1 How to use Cain & Abel to initiate a brute force attack
Brute force attack, is a cryptanalytic attack that can be used against any encrypted data. It consist of systematically checking all possible keys untill the correct key is found.
Que-2 Problems with using the brute force attack and compare & contrast with another password attack
Brute Force attack is more diverse as it checks all the possible combinations to crack password, however it takes a long time and sometimes this would involve traversing the entire search space.
Most password cracker tools offer hybrid modes, where they prefer words from a dictionary, test variations and finally test with brute forcing. The other almost same attack method is dictionary attack, they are not directly looking for a flaw or bypass, they’re guessing attacks. An online attack tries automated routines providing input to a legitimate system. An offline attack attempts to emulate the encryption/hashing and requires a known output of that process.
In brute force attack, the number of attempts is limited by the maximum length and the number of characters try per position, where as the dictionary or possible combinations is based upon some likely values and tends to exclude remote possibilities. It may be based on knowing key information about a perticular target.
The time to complete the brute force attack is greater, but there is a greater coverage of likely cleartext value.
Que-3 Justify the minimum requirements for a secure password policy.
Generally to secure a password, the minimum requirements are length, the characters chosen and some more combinations like using special characters and all. Mostly, people use their birth date or name as a password which is not a wise decision to have as it is quite easy to crack a password simply containing name or the details like birth date.
6. Encryption and Hashing
Cryptography
The method of converting the readable data into complex form which is not readable is called cryptography.
Hash Algorithm
It is a mathematical function used in cryptography to map data of arbitrary size to a hash of a fixed size.
Que-1 The use of MD5 hashes for Software downloads
MD5 hash comparison to verify file integrity for software downloads. MD5 is a commonly used algorithm for hashing which converts data into 128 bit hash value. The result of MD5 hash will be completely different even if there is a minor change in data. Checksum is the main function provided by MD5 to make sure the software installer validity.
Que-2 Difference between MD5 and SHA-1 hashes
These both hashing algorithms are intended to work one-way. So the data can only be verified by comparing the original hash value or specific data hash value.
MD5 is faster and has 128 bit output but SHA1 has 160 bit output.

Que-3 The use of SHA hashes for digital signatures in SSL certificates.
SHA algorithm is used by SSL/TSL certificate authorities to sign the digital certificates. When you buy a SSL certificate ,the certificate authority puts the digital signature on the SSL certificate and hashes using the SHA algorithm. The unique hash value is a proof that the SSL certificate is exactly the same as it was at the time of issuance, and the information it contains has not been modified or reproduced. If a third party person tries to manipulate the SSL certificate, the hash value of digital signature will be changed completely which alerts browsers and operating systems to the problem and they show an error warning to users.
5. Scanning and Remediating Vulnerabilities with OpenVAS
Objective:
OpenVAS
It is a vulnerability scanner that can detect security issues overall network. It is designed to be a self-contained vulnerability scanning framework. It is available as a source code and it is available as a virtual machine that can be compiled and installed on the existing machine.
SSL
SSL is a security protocol determines variables of the encryption for both the data and the link being transmitted.
Secure Socket Layer technology is used to establish an encrypted link between server and client to transfer the information securely.
Internet users have come to associate their online security with the lock icon that comes with an SSL-secured website or green address bar that comes with an Extended Validation SSL-secured website. SSL-secured websites also begin with https rather than http.
Que-1 Investigate and discuss one of the SSL vulnerabilities found as a result of the OpenVAS scan.
An OpenVAS scan executed in the server is at the security level of 5 and this scan shows the SSL vulnerability, a weak SSL cipher with 5.0 which is located on 3389
Que-2 Common Vulnerabilities and Exposures.(CVE) database.
It is a list of vulnerabilities and other information security exposures aiming to standardize the names for all generally known security and vulnerabilities exposures.
Facilitates data distribution within separate vulnerability databases and security tools. CSV is a file extension which makes searching for information in different databases easily. It is mostly based o key-words.
Hackers can break into a system by a software error called exposure.
Aspects in the list of CVE get names on the basis of the year of their formal inclusion & the order in which it was included in the list. The main purpose of CVE is to help sharing data across different security tools and databases.
Que-3 Steps to use vulnerability scanner to identify and re-mediate security issues.
We used OpenVAS scanner in this lab. The steps to use OpenVAS scanner is as follows:
- Turn on OpenVAS scanner in Kali OS and access GreenBone Security Assistant from web browser.
- Enter Credentials.
- Check the types of scans and services, and select the accordingly required type.(each type of scan provides different speed and depth of the scan).
- Go to Scan Management tab, select the purple wand button and then select advanced task wizard and fill the details of the scan.
- click on create task and then wait untill the scan task is completed.
- Once it is completed, the status will appear as done.
- Now click on report results to check the scan reports of the system.
4. Network Vulnerabilities Part-2
Objective: By comparing and contrast type of attacks, implement secure network architecture concept.
Denial of Services
As shown in the figure above, attacker uses pre-compromised PCs to target the main host to shut down the network or restart the network or aims to make the devices unavailable to the intended host by interrupting the normal functionality.
Anti-Phishing Toolbar
It has become need of an hour due to increasing phishing attacks. By using anti-phishing toolbar, the one can prevent unwanted online activities to avoid phishing attacks. There are few anti-phishing toolbars that are free to use and gives efficient results too. Some free anti-phishing toolbars are, Avira Browser(for Chrome & FireFox), Windows Defender Browser Protection(For Chrome),Avast Online Security(Chrome & FireFox), Bitdefender TrafficLight(Chrome,Firefox, Safari), Panda Safe Web(Chrome & Firefox), McAfee Secure Safe Browsing(Chrome) etc.
Que-1 Explain DOS attacks in your own words.
It is a cyber attack in which, a third person targets a system or device to make it unavailable for the legitimate user by interrupting devices normal functionality. It generally function by flooding a targeted system with requests until the normal traffic is unable to process.
DOS attacks fall in two categories: 1) Buffer-overflow attack can cause a machine to use all available hard disk space, memory and cpu-time. 2) Flood attacks saturates the targeted system by overwhelming the amount of packets or over-saturate server capacity.
Que-2 Explain in your words how the Hping3 attack causes the Denial of Services .
Hping3 is a network tool able to send custom TCP/UDP/ICMP packets. This also allows to do recon, possibly some basic exploitation too.
In the lab we used the following code to execute DoS attack
hping3 192.168.0.2 -p 80 -i u10 -S -q -rand-source
This code states that the given IP address will be flooded by SYN packets every 10 ms which will use random spoofed IP to the TCP port 80.
Que-3 Discuss the benefits of using anti-phishing functionality.
Anti-phishing functionalities can be classified into content filtering, Symptom-Based Prevention and Domain Binding.
It avoids the false positives by using content filtering
The functionality named, blacklist-based anti-phishing provides blacklist timing, quality and quantity
Prevents password-theft.
Provides Google-safe browsing
Provides Authentication-based anti-phishing functionality which provides URL verification
3. Network Vulnerabilities Part-1
Objective: Compare & contrast types of attacks, use appropriate S/W tools to access the security posture of an organization, analyse & interpret O/P from security technologies.
Network Footprinting: Footprinting is one of the pre-attack methods, which are performed before the actual attack to gain the information about the entities and computer systems they belong to. When the footprinting is passive, that means the sttacker is monitoring the traffic that is occuring between the device and other nodes. While in active footprinting, the attacker sends uniquely constructed packets to the device and monitors the response.
Packet Sniffing: Generally, data packets transmitted over the network in the from of blocks, cell, segment or a datagram. Packet sniffing is when third party tries to capture the data packets while transmitting. ISPs use this method to track activities like reciever of email, content of email, downloaded files, visiting sites, content of the sites, streaming events like videos, audios etc. For thi, they use packet sniffing to inject advertisements into flowing packets and mostly these advertisements contain malware.
Que-1 Summarize the information discovered in the lab about the network topology.
While using zenmap to analyse the network port, there are 7 systems(3 Linux and 5 Windows). There are six open ports and on the other side, linux systems are secured as it has less open ports.
While using Nmap scanning, the open ports are vulnerable points from which attack can happen.for security, scanning ports is an important aspect to make sure that the network is safe.
Que-2 How can packet sniffing be used to detect potential issues on network?
As we all say, ‘Every Coin has two sides’ same applies for packet sniffing, too.Packet sniffing can be used to monitor IP tracking, path analysis, bandwidth usage, port scanning etc. When it;s used for these purposes, it increases the overall performance and mitigates the time to check on every issue independently. As all these activities can be managed by one method and one node at a time to monitor and if there is any problem found in the network regarding IP tracking, path analysis, bandwidth usage, port scanning etc, it can be discovered easily by using packet sniffing.
Some government agencies also use packet sniffing to keep record for multiple purposes. most businesses use this for advertisements and of course the bad guys!!!!! also use it for malicious intentions.
According to me, having my traffic watched is not good at all for few reasons like risk of letting a third person know about my personal information through it.
Que-3 Analyse the captured packets from Exercise 2 and filter the DNS requests sent from 192.168.27.12 to 192.168.27.1 and view the UDP stream. What can you tell about DNS request?
Domain Name System is a proverbial glue that holds the internet together. DNS request is also lnown as DNS query. Generally, a host client send a request to DNS server to get the information about IP address associated with the DNS name.
UDP Stream : User Datagram Protocol is not a wise option to choose as it doesn’t check for errors but still is widely used for video conferencing, streaming audio and video, and for VoIP. It lowers the load on server. There is no need to send data packets individually as you can multicast it which makes the work simpler.
2. Application Data – Establish Host Security
Objective: Analyse and interpret output from security technologies.
Que-1 Discuss when you need to use Windows Defender feature from the lab. Windows Defender is free built-in software comes with WinXP and the higher versions. It is used to scan for malware and other potentially unwanted software. It is also used for virus and spyware definitions which comes in the form of files that can be used to identify the malicious and potentially unwanted software within the system.By default, It is set to scan automatically but then also sometimes it is needed to scan a full PC, which is by default set to a quick scan. In this particular lab, I explored windows defender in detail by trying on every options available for scan or updates and the interesting thing is whenever i want to check that which kind of malware or fictitious files had been discovered within the system and what steps were taken in the past, I can get the detailed information for that. It also offers firewall protection.
Que.2 Discuss a scenario when you need to use the online anti-malware scanner. There are plenty of anti-malware programs available online. Some of them are free of cost and to use some particular software program for anti-virus, it asks for some costs depends on the time period mainly, they also provide free trial for some days. In this lab, we are using online Microsoft security-scanner, which is free to use. According to me, it is same as windows defender. If the virus is interfering or disabled the current anti-virus program(for this lab its windows defender) the last resort you can try is online Microsoft safety/security scanner. In the given scenario, online Microsoft security scanner has been used to get the idea of online security software and that also means when the built-in security software faces problem scanning or removing the threat, a user can opt for online security options.
Que.3 Select a feature Internet Explorer Browser Security from the lab and discuss the reason it is required. There are various security features provided by Intertnet Explorer, ActiveX Filtering, InPrivate Browsing, Tracking Protection, SmartScreen Filter etc.
According to me, SmartScreen Filter is required as it it secures the System by warning whenever the user visits untrusted or malicious site. It identifies infected phishing and malware websites and also informs when the user downloads harmfully infectious file.
1.Social Engineering Reconnaissance
I have done the first lab of this subject, which is based on Social Engineering Reconnaissance.
So at first, What is Social Engineering? The answer is that, Social engineering is the practice of using non-technical means, to attack a target. Reconnaissance is basically gathering open source intelligence. During reconnaissance, SE will gather as much information on their target as possible.
Objective: Gather information from fictitious social media website MyBook to plan an attack by using social engineering reconnaissance techniques.
Question-1 Summerise the key information gathered from MyBook.
Mobilizing the information has become quite easy in this span because of the social media addiction of this age. Using social platform people share their information online from which critical data can be accessed by anyone to do dishonest.
Following is the basic information aggregated from MyBook account of a particular user.
- User Name : Phillip Nomad
- Nick Name : Phil
- Date of birth : 4th February 1990
- Spouse : Nina
- Phone Number : +44 (0)7704256110
- Education : Computer Science from Oxford University, UK
- Work Experience : Costa {Barista, August 2011-January 2014} HP {Software Development Internship Program, Jan 2014-Jan 2015} Google { Front End Software Engineer, Feb 2015 to Present}
- Languages : French(Beginner), English(Fluent)
- Address : Kingston upon Thames, London, UK
- Hobbies : Playing Guitar & taking care of his dog
Other information gathered from Phillip’s account:
- Phillip is quite famous and regular in updating the account as he has more than 1000 followers.
- His friends details can be easily accumulated as the friends list is public and it can be useful to find out more about Phillip.
- As he recently broke his car, its details can be collected from garage as he obviously would have visited a garage.
- Phillip has connections with well-settled personalities like CEO of an IT firm, Musician, Art & Graphic Designers.
- His Phone no. can be used to gather a bank details.
Question-2 : Risks of Using a Social Networking Platform.
Social media platforms are everywhere and seem to be able to do anything. They connect us to those we cannot be with personally. They travel the distance without seeming to cost anything at all to the user unless you opt to buy certain voluntary perks. They can allow voice and video chats to make the contact much more personal, but there are also hidden dangers lurking in these applications that you may not be aware of like Identity, Scams, Advertisement & Collecting your data. This can be prevented by being Assertive.
Common Social Media Security Risks:
- Unattended Social Media Accounts : It’s important not to ignore the accounts you don’t use yet, those that you’ve stopped using or those you don’t use often. This kind of accounts can be the target of hackers, who could start posting fraudulent messages under your name. Knowing the account is unmonitered, once they gain control, they could send anything from false information that’s damaging to your business to virus-infected links that could cause serious problem for followers and you won’t even notice until your customers start coming to you for help.
- Human Errors : Everyone makes mistakes. In today’s busy world, it is all too easy for an employee to accidentally expose the company to threats online. In fact, 77 % of respondents to the 20th EY(Ernst & Young) Global Information Security Survey said that a careless member of staff was the most likely source of a cyber-security threat. Something as simple as clicking on the wrong link or downloading the wrong file could wreak havoc.
- Third-Party Apps : Even if you have your own social accounts on lockdown, hackers may be able to gain access through vulnerabilities in third party apps that integrates with the big social network. For example, hackers gained access to the Twitter accounts of Forbes and Amnesty International using the flaw in Twitter Counter app, used for Twitter Analysis.
- Phishing-Attacks & Scams : Phishing is a type of social engineering attack, often used to steal user data, including login credentials and credit card numbers. It occurs when attacker masquerading as trusted entity, dupes a victim into opening an e-mail, instant message or text message. the recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, the freezing of the system as part of a ransomware attack or the revealing of a sensitive information. Moreover, phishing is often used to gain a foothold in a corporate or governmental network as a part of larger attack, such as Advanced Persistent(APT) Threat event. An organisation, succumbing to such an attack typically sustains severe financial loses in addition to declining market share, reputation and consumer trust. Depending on scope, a phishing attempt might escalate into security incident from which business will have a difficult time recovering.
- Impostor Accounts : Essentially, impostor accounts is an any social media account set up to impersonate another individual or business, whether directly or indirectly. This account could be monitored by a person or potentially by a ‘hot’ which is an automatic computer program developed to carry out certain actions. Impostor accounts are used to : Impersonate influential individuals and criticize, mock or lie about company activities.
Pretend to be a company or employee and damage brands through unsavory comments and posts.
Create and exploit security vulnerabilities like gaining access to sensitive data or business accounts.
Conduct phishing schemes or other scam activities . - Malware Attacks and hacks : Social Media hackers are becoming more sophisticated. Malware is any software intentionally designed to cause damage to a computer, server, client, or computer network. Malware does the damage after it is implanted or introduced in some way into a target’s computer and can take the form of directly executable codes, scripts, and other forms of data. Programs officially supplied by companies can be considered malware if they secretly act against the interest of computer user. For Instance, at one point, Sony music compact disks silently installed a rootkit on purchasers’ computer running Microsoft Windows with the intention of preventing illicit copying, but which also reported on users listening habits and unintentionally created extra security vulnerabilities.
- Privacy Setting : People seem to ell-aware of potential privacy risks of using social media.One US survey found that nearly two-third people have ‘very-little’ or ‘no trust’ in social networks when it comes to privacy protection. But those concern doesn’t stop us from using our favorite social channels.
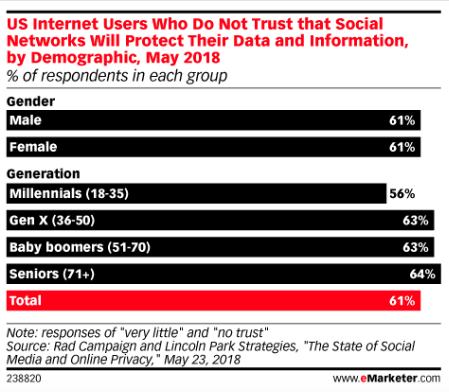
8. Unsecured Mobile Phones : Mobile devices are the most popular way to access social networks. Using, each network’s mobile app makes it easy to access social media account with just one tap. Protecting a device with a password helps, but more than half of mobile phone users leave their phone unlocked. That’s great as long as your phone stays in your possession. But if your phone or an employee’s phone, is lost or stolen, one-tap access makes it easy for a thief to access social accounts.
Question-3 How the information gathered can be leveraged to attack an organisation?
- Phillip is working as a creative director at google. Generally, employees working as creative director in an organisation have “Root-Level Access” to all the domain and server files as well as payment details since it is a part of their employment description. Hackers continue to rely on a tried-and-true method to steal personal data and rip people off-phishing that follows current news and trends. Criminal continue to be successful, thinking goes, because phishing attacks are simple, low-tech and exploit weaknesses in human nature. It can help the attacker to gain access to Banking Details, Text Permissions, Admin Privileges, Account Access, etc. Even internet giants like Google and Facebook got duped out of $100M through an email phishing scheme when a hacker impersonated a computer-parts vendor.
- A Personal Phone Number also has been shared by him on the social media account. It can be used by an attacker for ‘Bogus Surveys’ , ‘Charity Requests’ or ‘Tech-Support Scams’.
- The friend-list includes some well-designated personalities and the information of Phil’s friend-list can be assessed as it has not been set to private. The security concerns may raise on those personalities as well.
- Location is also pin-pointed on the MyBook website which can be used by a criminal during his working or non-working hours i n any manner.
- Forged Advertisements also can be used to get Phillip in trust as he is a beginner in learning French. Attacker can scheme him in low-cost french classes and might get successful in getting the information he want.